 Selasa, 15 April 2025 (01:21)
Selasa, 15 April 2025 (01:21)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
THM | Buffer overflow in 8 min (Incendium) View |
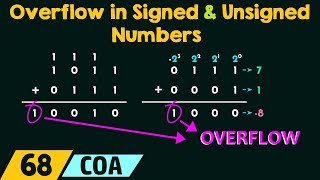 |
Overflow in Signed and Unsigned Numbers (Neso Academy) View |
 |
how do hackers exploit buffers that are too small (Low Level) View |
 |
Buffer Overflows Made Easy - Part 1: Introduction (The Cyber Mentor) View |
 |
What Is BUFFER OVERFLOW | Overflow Of Input | Programming Errors Explained (Bitten Tech) View |
 |
Buffer Overflows: History and Motivation (Sourcefire) View |
 |
What is a Stack Buffer Overflow Exploring How To Exploit the Stack (Dr Josh Stroschein - The Cyber Yeti) View |
 |
TryHackMe Buffer Overflow prep OVERFLOW9 (Jek1ll\u0026\u0026Hyd3) View |
 |
Practical exploitation of a Buffer Overflow vulnerable C program (Engineer Man) View |
 |
Buffer Overflow (osama kamal) View |